This time we participated in AUCTF 2020. It was very fun. Thanks to organizers!
[OSINT] Who made me
One of the developers of this CTF worked really hard on this challenge.
note: the answer is not the author’s name
Author: c
Solution:
After search by keywords "AUCTF 2020" we found repositories on GitHub.
Checking the commits we found the flag:
[OSINT] Good Old Days
Task:An OSINT challenge using wayback archive
Prompt: This site used to look a lot cooler.
Author: c
Solution:
After checking the Wayback Machine site https://web.archive.org/ we found the record in the sitemap for CTF site.
[OSINT] ALIedAS About Some Thing
Task:See what you can find.
AUCTFShh
Author: c
Solution:
First we tried to check AUCTFShh as the username.We used https://namechk.com/ for this activity.
Steam account https://steamcommunity.com/id/AUCTFShh gave us the alias youllneverfindmese.
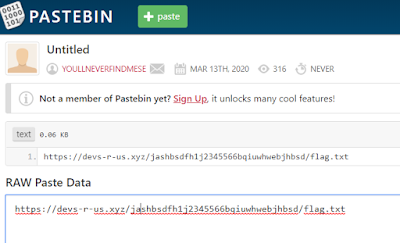
Looking again NameCheck site for youllneverfindmese we found Pastebin page with link.
[OSINT] Oxyr
Task:
One of the developers of devs-r-us.xyz has been a little sketchy lately. We have received reports that they may be selling data to competitors. We just haven’t found out how!
Author: c
Solution:
Site https://devs-r-us.xyz/ has several files.
We discovered the site pages and found link to hidden page:
<button class="btn btn-primary" data-toggle="modal"
onclick="location.href='1ndex.html#share-section'">Contact Us</button>
The source code of 1ndex.html:
<div class="py-4">
<h1 class="h3">Devs-R-Us</h1>
<p>Copyright © 2020</p>
<button class="btn btn-primary" data-toggle="modal" data-target="#contactModal">Contact Us</button>
<!-- 'Who is MaddAddam?' -->
</div>
We found several png-images:
- mcafee.png
- mcofee.png
We checked the metadata:
$ exiftool mcafee.png
And got next information:
Description: https://discord.gg/pMzcE45 DM me if you want more info
After deep examination of site, we tried to use several names Jorge Greenwood and
Loretta Mcintosh to find them at Discord.
After conversation with Jorge G we got the QRcode with the link to flag.
[OSINT] OSINT You All Other The Place
Task:This company is super cool! You should see who made it.
http://devs-r-us.xyz
author c
Solution:
We checked the information for this domain:
$ whois devs-r-us.xyz
As domain registered on namecheap, we checked our domain there
https://www.namecheap.com/domains/whois/result?domain=devs-r-us.xyz
We got next information:
Admin Email: admin@devs-r-us.com
Registrant Email: shannonengrid@gmail.com
Registrant Phone: +1.3343844504
Searching by shannonengrid we found the Instagram account with one post:
And we saw the auctf in the text, so we got the flag: auctf{7sbhww4yt0g0ONf1nd1nGth3fl4G}
[Web] gg no re
Task:http://challenges.auctf.com:30022
A junior dev built this site but we want you to test it before we send it to production.
Author: shinigami
Solution:
Main page has next code:
<html>
<head>
<script>authentication.js</script>
</head>
<body>
<center><h1>Nothing to see here</h1></center>
</body>
</html>
We checked js-file http://challenges.auctf.com:30022/authentication.js:
var _0x44ff=['TWFrZSBhIEdFVCByZXF1ZXN0IHRvIC9oaWRkZW4vbmV4dHN0ZXAucGhw','aW5jbHVkZXM=','bGVuZ3Ro','bG9n'];(function(_0x43cf52,_0x44ff2a){var _0x2ad1c9=function(_0x175747){while(--_0x175747){_0x43cf52['push'](_0x43cf52['shift']());}};_0x2ad1c9(++_0x44ff2a);}(_0x44ff,0x181));var _0x2ad1=function(_0x43cf52,_0x44ff2a){_0x43cf52=_0x43cf52-0x0;var _0x2ad1c9=_0x44ff[_0x43cf52];if(_0x2ad1['UmZuYF']===undefined){(function(){var _0x4760ee=function(){var _0x335dc0;try{_0x335dc0=Function('return\x20(function()\x20'+'{}.constructor(\x22return\x20this\x22)(\x20)'+');')();}catch(_0x3b3b3e){_0x335dc0=window;}return _0x335dc0;};var _0x1ecd5c=_0x4760ee();var _0x51e136='ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=';_0x1ecd5c['atob']||(_0x1ecd5c['atob']=function(_0x218781){var _0x1c7e70=String(_0x218781)['replace'](/=+$/,'');var _0x1fccf7='';for(var _0x2ca4ce=0x0,_0x55266e,_0x546327,_0x17b8a3=0x0;_0x546327=_0x1c7e70['charAt'](_0x17b8a3++);~_0x546327&&(_0x55266e=_0x2ca4ce%0x4?_0x55266e*0x40+_0x546327:_0x546327,_0x2ca4ce++%0x4)?_0x1fccf7+=String['fromCharCode'](0xff&_0x55266e>>(-0x2*_0x2ca4ce&0x6)):0x0){_0x546327=_0x51e136['indexOf'](_0x546327);}return _0x1fccf7;});}());_0x2ad1['hdhzHi']=function(_0x5d9b5f){var _0x24b0b1=atob(_0x5d9b5f);var _0x5c5f21=[];for(var _0x390988=0x0,_0xd8eac0=_0x24b0b1['length'];_0x390988<_0xd8eac0;_0x390988++){_0x5c5f21+='%'+('00'+_0x24b0b1['charCodeAt'](_0x390988)['toString'](0x10))['slice'](-0x2);}return decodeURIComponent(_0x5c5f21);};_0x2ad1['wrYKfR']={};_0x2ad1['UmZuYF']=!![];}var _0x175747=_0x2ad1['wrYKfR'][_0x43cf52];if(_0x175747===undefined){_0x2ad1c9=_0x2ad1['hdhzHi'](_0x2ad1c9);_0x2ad1['wrYKfR'][_0x43cf52]=_0x2ad1c9;}else{_0x2ad1c9=_0x175747;}return _0x2ad1c9;};function authenticate(_0x335dc0){if(validate(_0x335dc0)){console[_0x2ad1('0x2')](_0x2ad1('0x3'));}};function validate(_0x3b3b3e){return _0x3b3b3e[_0x2ad1('0x1')]>=0x5&&_0x3b3b3e[_0x2ad1('0x0')]('$');}
After base64 decoding for
var _0x44ff=['TWFrZSBhIEdFVCByZXF1ZXN0IHRvIC9oaWRkZW4vbmV4dHN0ZXAucGhw','aW5jbHVkZXM=','bGVuZ3Ro','bG9n'];
we got:
var _0x44ff=['Make a GET request to /hidden/nextstep.php','includes','length','log'];
After following the link we got next HTTP response:
HTTP/1.1 200 OK
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/7.0.33
ROT13: Znxr n CBFG erdhrfg gb /ncv/svany.cuc
Content-Length: 15
Connection: close
Content-Type: text/html; charset=UTF-8
Howdy neighbor!
We decripted data in the ROT13 header and got:
Make a POST request to /api/final.php
Response was following:
HTTP/1.1 200 OK
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/7.0.33
Content-Length: 43
Connection: close
Content-Type: text/html; charset=UTF-8
Send a request with the flag variable set
So we got the flag:
POST /api/final.php HTTP/1.1
Host: challenges.auctf.com:30022
flag=test
HTTP/1.1 200 OK
Server: Apache/2.4.25 (Debian)
X-Powered-By: PHP/7.0.33
Content-Length: 30
Connection: close
Content-Type: text/html; charset=UTF-8
auctf{1_w@s_laZ_w1t_dis_0N3}
[Web] Miyazaki Trivia
Task:http://challenges.auctf.com:30020
Here's a bit of trivia for you vidya game nerds.
Author: shinigami
Solution:
When we opened the site, we had the message:
Find this special file.
So we tried robots.txt:
VIDEO GAME TRIVIA: What is the adage of Byrgenwerth scholars?
MAKE a GET request to this page with a header named 'answer' to submit your answer.
We googled for the answer, it was "Fear the Old Blood", so we send the following request
GET /robots.txt HTTP/1.1
Host: challenges.auctf.com:30020
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
answer: Fear the Old Blood
![AUCTF2020] Writeups](https://media.vlpt.us/images/woounnan/post/c48c25cc-1be5-49d4-9bbc-b88128e91c29/logo-auctf.png)